('Master' ' dual desktop via Mandolux)
My brain is still swimming in whole disk encryption issues from the past week at work.
Found these links particularly insightful or amusing; maybe both.
- Cracking budget encryption - heise Security UK ' Really great and extended article that show the process by which researchers analyzed and broke the on-board encryption methods used by a particular USB hard-drive system. It is great analysis work and might be useful from a forensics perspective as well.
- Hard Drive Passwords Easily Defeated; the Truth about Data Protection - Computer Technology Review: Data Storage and Network Solutions. Great (though a bit old) whitepaper post on different strategies and techniques used in drive encryption. Software-based whole-disk encryption is the strongest solution currently available. Using the firmware-based HDD locking might seem like a fast and easy solution, but law-enforcement and data-recovery specialists can bypass this with a bit of effort.
- What happens when you overwrite data? - SANS Computer Forensics, Investigation, and Response. Update by Dr. Craig Wright on the mechanics when data is overwritten and recovery is attempted. Nice images and very readable. Continues to expand his Overwriting Hard Drive Data post earlier presented by Dr. Wright at the same blog.
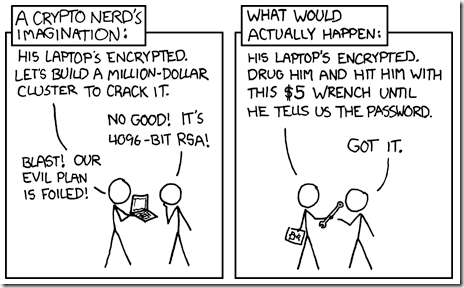
- Security ' As found on the always geeky and insightful xkcd webcomic blog
Other Personal Observations:
Having a cool security sticker/label on you systems that lets everyone know your system is encrypted offers no security if the system is a laptop and 'lifted' while it is running and not locked down.
Just because the label says it is encrypted it in no way guarantees that the drive itself has actually been encrypted. Security auditors still have to log and verify by accessing the system that the encryption solution has been correctly applied to the drive(s). If a technician images the system and forgets to apply the encryption solution (if not automatically deployed via system policies), the sticker provides a false and dangerous sense of security completion and protection for both management and the end-user.
While a properly encrypted system does protect and guard the data on the hard-drive itself, it
- Doesn't mean that the data can't be easily lifted by malware/trojan running on the system when the system is live and operating in an 'unencrypted' mode,
- Doesn't mean that the system no longer has 'theft value' as someone could remove and discard the drive, drop in a replacement and sell the sucker at a pawn shop or eBay,
- Doesn't mean that the data is protected enterprise-wide if the data is accessed/replicated across various desktop/laptop systems in the organization and any one of those systems escapes the disk-encryption process,
- Doesn't help anything if people keep their access password or passphrase taped under their keyboard, to their monitor, or cpu base.
I'm fully supportive and highly value properly applied whole-disk encryption solutions. However, it must be seen as just one more hardened layer of protection among many in a properly configured and applied organizational computer security structure.
--Claus V.
Read More...
[Source: Grand Stream Dreams - Posted by Kishore Vengala]

No comments:
Post a Comment